? ? ?
今天闲来无事在Google上搜关键词tianhaoo的时候,发现一个域名www.tmmdd.com解析到了我的IP地址120.79.74.49的80端口上。
???
别人的域名解析到了我的IP地址??

听说有过这样的操作,把自己的域名解析到别人的 IP ,就相当于原样复制了一个别人的内容丰富的站点,这个域名被搜索引擎(主要指谷歌)后, 就能够短时间内得到别人的权重( PR 值),然后有权重的域名是可以卖钱的,不过后来搜索引擎能够识别这种方式了。
而且
我这只是个放作业的小站啊,几百年没人访问一次,能有啥PR??

为什么还会有这种事情发生?你拿着钱去买的域名就是为了解析到别人的IP上面去的吗?不拿去干点正事的吗?

- 搜了下域名信息
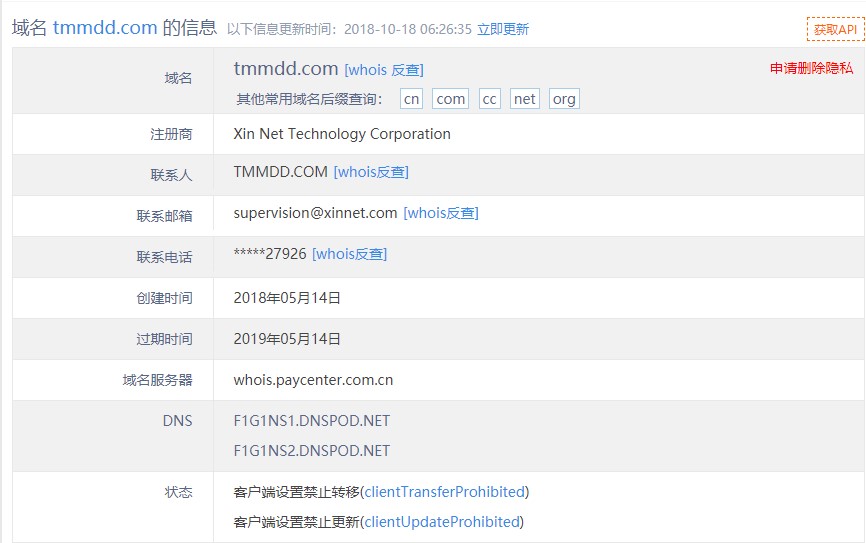
- Raw Whois Data
Domain Name:tmmdd.com Registry Domain ID:2263175751_DOMAIN_COM-VRSN Registrar WHOIS Server:whois.paycenter.com.cn Registrar URL:http://www.xinnet.com Updated Date:2018-05-14T09:33:14.00Z Creation Date:2018-05-14T09:33:14.00Z Registrar Registration Expiration Date:2019-05-14T09:33:14.00Z Registrar:XINNET TECHNOLOGY CORPORATION Registrar IANA ID:120 Registrar Abuse Contact Email:email@xinnet.com Registrar Abuse Contact Phone:+86.1087128064 Reseller:DNSPod Domain Status: Registry Registrant ID: Registrant Name: Registrant Organization: Registrant Street: Registrant City: Registrant State/Province: Registrant Postal Code: Registrant Country: Registrant Phone: Registrant Phone Ext: Registrant Fax: Registrant Fax Ext: Registrant Email: Registry Admin ID: Admin Name: Admin Organization: Admin Street: Admin City: Admin State/Province: Admin PostalCode: Admin Country: Admin Phone: Admin Phone Ext: Admin Fax: Admin Fax Ext: Admin Email: Registry Tech ID: Tech Name: Tech Organization: Tech Street: Tech City: Tech State/Province: Tech PostalCode: Tech Country: Tech Phone: Tech Phone Ext: Tech Fax: Tech Fax Ext: Tech Email: Name Server:f1g1ns1.dnspod.net Name Server:f1g1ns2.dnspod.net DNSSEC:unsigned URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/ >>> Last update of WHOIS database: 2019-04-07T09:17:18.00Z «<:
For more information on Whois status codes, please visit https://icann.org/epp
The Data in Paycenter’s WHOIS database is provided by Paycenter for information purposes, and to assist persons in obtaining information about or related to a domain name registration record. Paycenter does not guarantee its accuracy. By submitting a WHOIS query, you agree that you will use this Data only for lawful purposes and that, under no circumstances will you use this Data to: (1) allow, enable, or otherwise support the transmission of mass unsolicited, commercial advertising or solicitations via e-mail (spam); or (2) enable high volume, automated, electronic processes that apply to Paycenter or its systems. Paycenter reserves the right to modify these terms at any time. By submitting this query, you agree to abide by this policy.!!
- HTTP状态查询
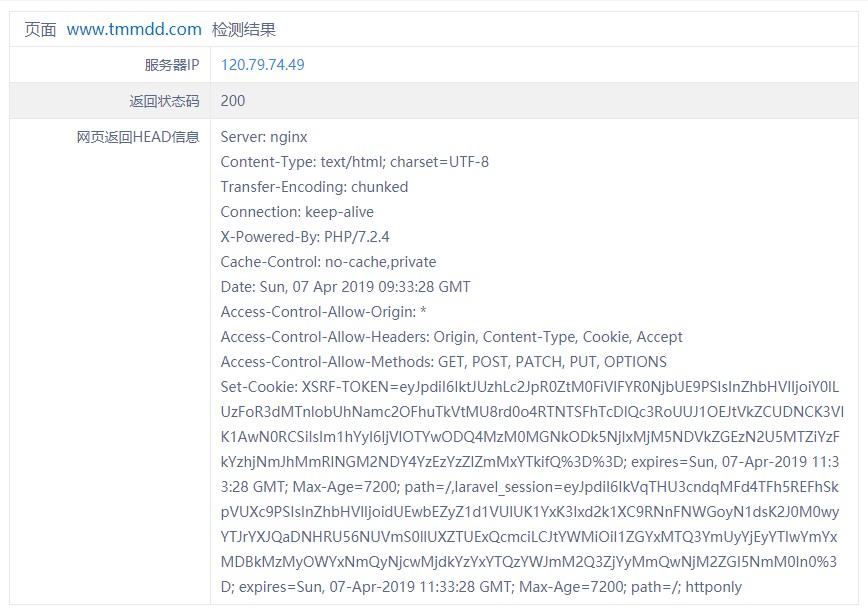
- Google了下
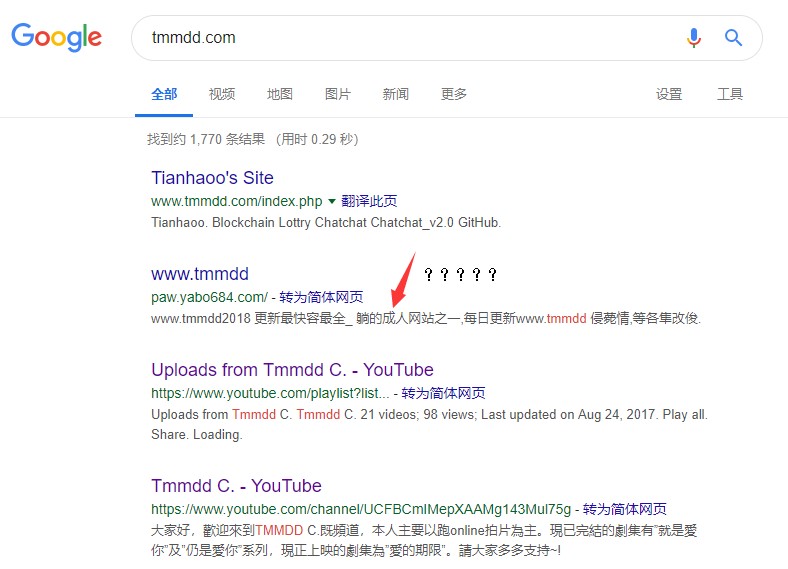
W…What?

举报走一波
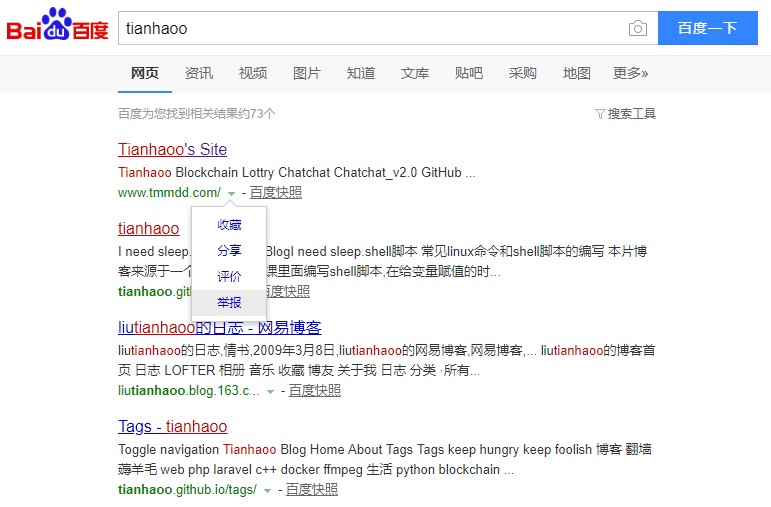
防治恶意跳转
使用nginx
nginx中自带一些变量可以起到判断用户域名、IP等的作用,也可以用allow、deny设置黑白名单。
$host变量
host变量的值按照如下优先级获得:
- 请求行中的host.
- 请求头中的Host头部.
- 与一条请求匹配的server name.
$http_referer变量
$http_referer 表示的是 HTTP_REFERER 这个HTTP头.
使用PHP
$_SERVER[‘HTTP_REFERER’]变量存储host信息,只要对这个变量做一下判断即可
例如:
if ($_SERVER['HTTP_REFERER'] == 'his_stie.com') {
header('HTTP/1.0 403 Forbidden');
exit;
}
结果
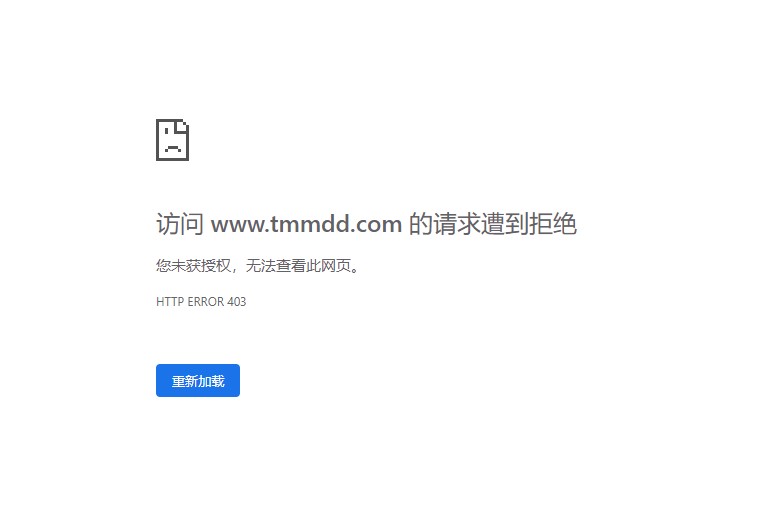
看了网友的做法,我觉得我给他返回403已经算仁慈的了。。。
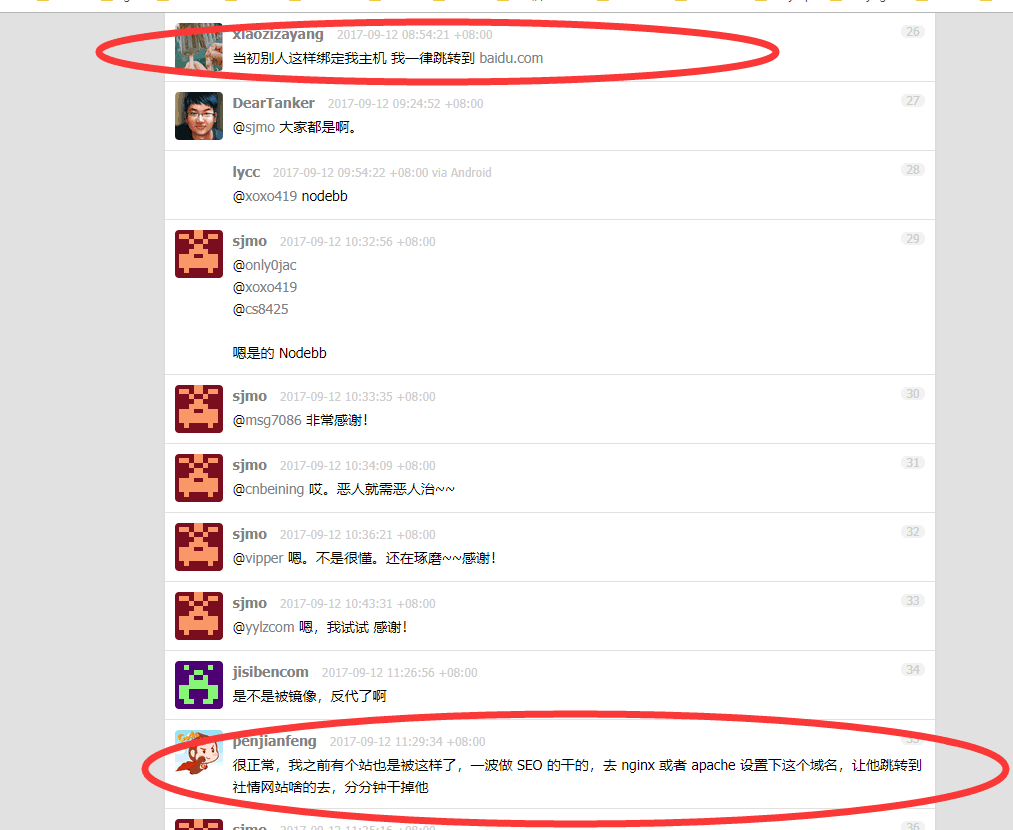
参考: